Technology
Unlocking the Potential: Prekldača in Electrical Circuits
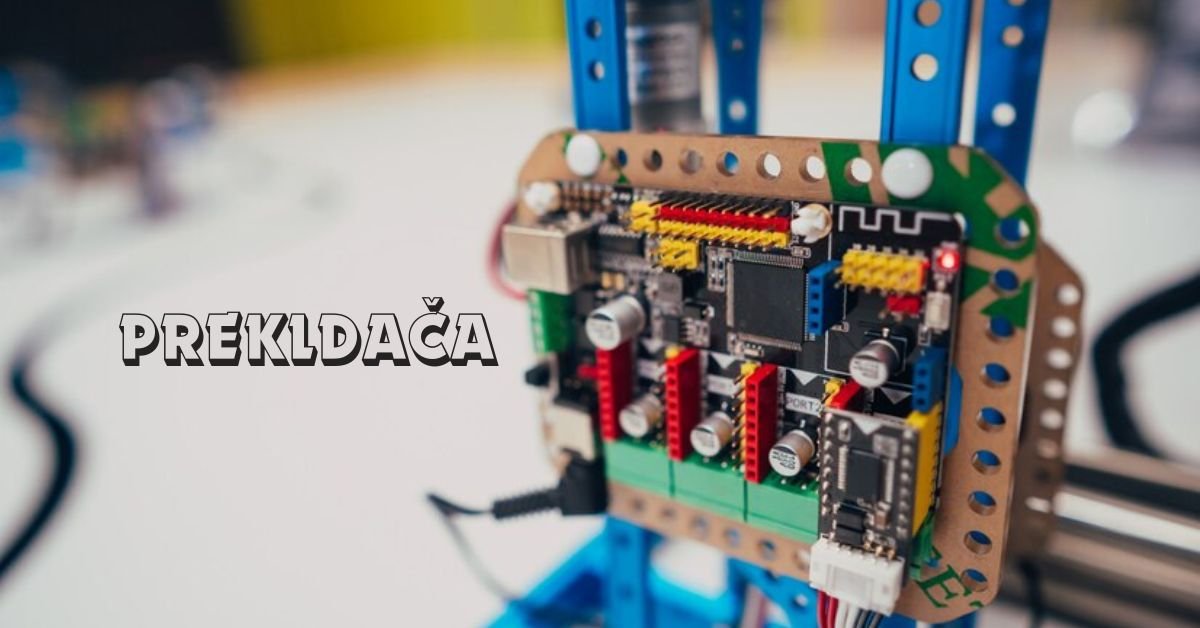
In the realm of electrical engineering, the Prekldača stands as a fundamental component in controlling the flow of current within circuits. Its name originates from the Slovak word “prekldať,” meaning “to switch.” The term “Prekldača” encompasses various devices used to manage the flow of electricity, ranging from simple mechanical switches to sophisticated solid-state relays.
Understanding the Functionality of Prekldača
Definition of Prekldača
At its essence, a Prekldača serves as a gateway that can either complete or interrupt an electrical circuit. It consists of one or more contacts that can be opened or closed to control the flow of current. The operation of Prekldača is governed by the principles of electromagnetism, where the application of an electrical signal triggers a mechanical or electronic action.
Types of Prekldača
Prekldača comes in various types, each tailored to specific applications and requirements. Mechanical switches, such as toggle switches and push-button switches, rely on physical mechanisms to make or break electrical connections. Solid-state relays utilize semiconductor devices like transistors to achieve similar switching functionality without moving parts, offering advantages such as faster switching speeds and longer lifespan.
Importance of Prekldača in Electrical Circuits
The importance of Prekldača in electrical circuits cannot be overstated. It serves as the primary means of controlling the operation of devices and systems, from simple household appliances to complex industrial machinery. Without Prekldača, it would be challenging to regulate the flow of electricity, leading to inefficiencies, safety hazards, and malfunctioning equipment.
How Prekldača Works
Basic Principles
The operation of Prekldača revolves around the interaction between electrical currents and magnetic fields. When an electrical signal is applied to the Prekldača, it energizes coils or electronic circuits, generating magnetic fields that attract or repel movable contacts. This action either completes the circuit, allowing current to flow, or opens the circuit, halting the flow of current.
Components and Construction
Prekldača comprises several essential components, including contacts, coils, actuators, and housings. The contacts, typically made of conductive materials like copper or silver, establish electrical connections when closed and prevent current flow when open. Coils or electronic circuits provide the necessary magnetic fields to control the movement of contacts, while actuators facilitate manual or automatic operation. The housing encloses these components, providing protection and insulation.
Applications of Prekldača
Prekldača finds applications across a wide range of industries and sectors:
- Residential: In homes, Prekld’ača controls lighting systems, fans, heaters, air conditioners, and kitchen appliances.
- Commercial: In commercial settings, Prekld’ača regulates power distribution, HVAC systems, security alarms, and access control systems.
- Industrial: In industrial environments, Prekld’ača is integral to machinery control, motor starters, process automation, and power management systems.
Advantages of Using Prekldača
The utilization of Prekldača offers numerous benefits:
- Flexibility: Prekld’ača provides precise control over electrical circuits, allowing for on-demand operation.
- Safety: Prekld’ača incorporates safety features such as overload protection, short-circuit protection, and arc suppression.
- Energy Efficiency: By effectively managing the flow of current, Prekld’ača helps optimize energy consumption and reduce waste.
- Reliability: Well-designed Prekld’ača ensures reliable performance, even under challenging conditions such as high temperatures or voltage fluctuations.
- Compatibility: Prekld’ača is compatible with various voltage and current ratings, making it adaptable to diverse applications.
Challenges and Considerations
Despite its advantages, the implementation of Prekld’ača poses certain challenges:
- Reliability: Mechanical switches may wear out over time, leading to decreased reliability and performance.
- Compatibility: Integrating Prekld’ača into complex circuits requires careful consideration of compatibility issues with other components.
- Cost: High-performance Prekld’ača with advanced features may incur higher costs, impacting project budgets.
- Regulatory Compliance: Prekld’ača must adhere to safety standards and regulations to ensure proper operation and minimize risks.
Future Developments in Prekldača Technology
As technology continues to evolve, the future of Prekld’ača holds promise for advancements in:
- Efficiency: Innovations in materials and design techniques may lead to more energy-efficient Prekld’ača with reduced power losses.
- Reliability: Research into robust materials and manufacturing processes could enhance the reliability and lifespan of Prekld’ača.
- Smart Functionality: Integration of smart features such as remote control, sensor feedback, and network connectivity may enable more sophisticated Prekld’ača for IoT and automation applications.
Conclusion
In conclusion, Prekld’ača plays a pivotal role in the field of electrical engineering, providing essential control and management capabilities for circuits and systems. Its versatility, reliability, and efficiency make it indispensable across various industries and applications. As technology progresses, the evolution of Prekld’ača is expected to drive further innovations, shaping the future of electrical control systems.
FAQs
- What is the difference between a Prekldača and a regular switch?
A Prekld’ača encompasses various types of switches, including mechanical and electronic switches, offering more versatility and functionality than a standard on-off switch. - Can Prekldača be used in high-voltage applications?
Yes, Prekld’ača is available in configurations suitable for high-voltage applications, with designs optimized for safety and reliability. - How do I choose the right type of Prekldača for my circuit?
Consider factors such as voltage and current ratings, switching speed, environmental conditions, and required features when selecting a Prekld’ača for your application. - Are there any safety precautions to consider when using Prekldača?
Always follow manufacturer guidelines and relevant safety standards when installing and operating Prekld’ača to prevent electrical hazards and ensure proper functionality. - What are some common troubleshooting techniques for Prekldača issues?
Check for loose connections, damaged components, or signs of overheating. Testing continuity and voltage levels can also help identify and resolve Prekld’ača problems.
Technology
Seamlessly Install KDE on AlmaLinux: A Quick Guide

Introduction To KDE And AlmaLinux
KDE is one of the most popular desktop environments for Linux users, and for good reason. Its sleek design, extensive customization options, and powerful features make it a favorite among both beginners and seasoned professionals.
On the other hand, AlmaLinux has emerged as a go-to choice for those seeking stability and reliability in an enterprise-grade operating system. Combining these two can create an exceptional computing experience.
If you’re looking to breathe new life into your AlmaLinux setup, installing KDE could be just what you need. Whether you’re drawn in by its vibrant aesthetics or the promise of seamless functionality, this guide will help you navigate the installation process effortlessly. Get ready to transform your workspace with a desktop environment that suits your style perfectly!
TRENDING
Harmony Of Modernism: Eastern Aesthetic Fusion
Benefits Of Using KDE On AlmaLinux
KDE on AlmaLinux offers a sleek and modern desktop experience. This combination provides a polished interface that enhances productivity without sacrificing performance.
One of the standout features is customization. Users can tailor their desktops to fit individual preferences, from widgets to themes. This flexibility makes it appealing for both new users and experienced developers.
Additionally, KDE’s rich application ecosystem integrates seamlessly with AlmaLinux. Popular applications like Krita and Kdenlive run smoothly, allowing creative projects to flourish.
Another benefit is robust community support. The active forums and documentation help troubleshoot issues quickly, ensuring smooth sailing as you navigate your Linux journey.
Security also shines in this setup. With AlmaLinux’s enterprise-grade stability paired with KDE’s regular updates, users enjoy peace of mind knowing their system remains secure against vulnerabilities while staying up-to-date with software enhancements.
System Requirements For Installing KDE On AlmaLinux
Before diving into the installation, it’s essential to check your system requirements for KDE on AlmaLinux. This ensures a smooth experience and optimal performance.
KDE is known for its rich features; thus, it demands certain hardware capabilities. A minimum of 2 GB RAM is recommended. However, having 4 GB or more will provide better responsiveness, especially if you plan to run multiple applications simultaneously.
For storage space, at least 10 GB should be allocated just for the KDE desktop environment. It’s wise to have additional space for your files and applications as well.
A modern processor (Intel or AMD) can significantly enhance your user experience with KDE’s graphical interface. Keeping these specifications in mind will help you enjoy all that KDE has to offer seamlessly on AlmaLinux!
Step-By-Step Guide To Installing KDE On AlmaLinux
To install KDE on AlmaLinux, begin by updating your system. Open the terminal and run:
“`bash sudo dnf update“`
Next, you’ll want to enable the EPEL repository. This can be done with:
“`bash sudo dnf install epel-release“`
Now it’s time to get KDE installed. Use this command:
“`bash sudo dnf groupinstall “KDE Plasma Workspaces”“`
After the installation completes, set KDE as your default environment by running:
“`bash echo “exec startkde” > ~/.xinitrc“`
You may need to reboot for changes to take effect. Simply type:
“`bash reboot“`
Once back online, select ‘Plasma’ from the session options at the login screen.
Log in and enjoy exploring all that KDE has to offer!
Customizing And Personalizing KDE On AlmaLinux
Customizing KDE on AlmaLinux opens a world of possibilities. The desktop environment is known for its flexibility and user-friendly interface, allowing you to tailor it to fit your needs perfectly.
Begin by exploring the System Settings menu. Here, you can modify themes, icons, and fonts with just a few clicks. Choose from pre-installed options or download new ones from online repositories.
You can also arrange panels and widgets according to your workflow preferences. Adding weather forecasts, system monitors, or task lists enhances productivity without cluttering your desktop.
Don’t forget about keyboard shortcuts! Personalize them for improved efficiency when navigating through applications or performing tasks quickly.
Dive into KDE’s extensive library of applications tailored to different areas like multimedia editing or office productivity. This further enriches your experience on AlmaLinux while keeping everything cohesive and streamlined.
Troubleshooting Common Issues With KDE On AlmaLinux
Encountering issues with KDE on AlmaLinux can be frustrating, but many problems have straightforward solutions. One common issue is slow performance after installation. This might stem from insufficient hardware resources or misconfigured settings. Ensure your system meets the recommended requirements and consider adjusting visual effects for better speed.
Another frequent challenge involves missing applications or libraries. If you notice certain software is not functioning correctly, check whether dependencies are installed properly. Using package managers like DNF can simplify this process.
If KDE fails to launch altogether, try booting into a different session via the login screen. You may need to reinstall or update specific components if that doesn’t resolve the issue.
Keep an eye on forums and community discussions about any bugs in recent updates. The open-source community often shares quick fixes that could save you time and effort in troubleshooting your setup.
Conclusion
KDE and AlmaLinux together create a powerful combination for users seeking an efficient and visually appealing desktop experience. The flexibility of KDE allows you to customize your environment, making it easier to tailor your workflow.
Installing KDE on AlmaLinux is straightforward, especially with the step-by-step guide provided. Whether you’re a seasoned user or just starting out, you’ll find that the system requirements are manageable and the installation process simple enough to follow.
Once you’ve installed KDE, personalizing it can enhance your productivity even further. With various themes and widgets available, you can make your desktop truly yours.
If any issues arise during installation or usage, remember that troubleshooting common problems is often just a quick search away. Most challenges have been faced by other users before you and solutions are readily available in community forums.
Embracing KDE on AlmaLinux opens up new possibilities for both work and play. It’s time to explore what this dynamic duo has to offer!
ALSO READ: Mining Bittensor In The Cloud: A New Frontier
FAQs
What is “AlmaLinux install KDE”?
“AlmaLinux install KDE” refers to the process of installing the KDE Plasma desktop environment on AlmaLinux, an enterprise-grade Linux distribution. This involves updating your system, enabling the EPEL repository, and using package management commands to install KDE Plasma Workspaces. The result is a sleek and customizable desktop experience on your AlmaLinux setup.
What are the key benefits of using KDE on AlmaLinux?
KDE on AlmaLinux provides a modern and customizable desktop interface that enhances productivity and performance. Benefits include a highly configurable workspace, integration with KDE’s rich application ecosystem, strong community support, and robust security features.
What are the system requirements for installing KDE on AlmaLinux?
To install KDE on AlmaLinux, you should have a minimum of 2 GB of RAM (4 GB or more recommended), at least 10 GB of storage space for the desktop environment, and a modern Intel or AMD processor for optimal performance.
How do I customize KDE on AlmaLinux after installation?
After installing KDE, you can customize it by exploring the System Settings menu to change themes, icons, and fonts. You can also arrange panels and widgets to suit your workflow, and set up keyboard shortcuts to enhance efficiency.
What should I do if KDE on AlmaLinux is running slowly or has issues?
If KDE runs slowly or encounters issues, check if your system meets the recommended hardware requirements and consider adjusting visual effects for better performance. Ensure that all necessary dependencies are installed correctly and consult community forums for potential fixes and troubleshooting advice.
Technology
4 Ways AI Is Transforming Online Businesses

As inflation continues to ravage the average consumer’s purchasing power, brick-and-mortar businesses are forced to adapt to the ever-changing times. That’s why they are switching to online to save and maintain their bottom lines and keep pace with consumer habits. Also, going online is a cost-saving move for many online businesses. One way these businesses are saving money is by having AI take the lead on the day-to-day operations.
1. More Efficient Cybersecurity
It doesn’t matter if you’re running a basic blog and selling a few products on your website or you’re a major online retailer like Amazon, everyone is vulnerable to cyberattacks. Online businesses rely on AI to handle their cybersecurity needs more than ever. AI first bolsters online security by checking the current network for loopholes and vulnerable spots.
The second way is to perform a deep authentication analysis for new members. When joining today’s popular online sites, it’s common to perform a deep analysis of the registration form. By requiring parts of a member’s social security number, residential address, and essential biometrics like photos and copies of photo identification, AI greatly helps online businesses prevent bad actors from entering their networks.
But even when members are successfully registered, AI’s cybersecurity duties don’t stop. Online businesses use AI for multi-factor authentication to ensure that only authenticated members gain access to the network. An online member might receive a PIN on their phone or email to verify their online business or gaming account.
2. Customer Support
Having a reliable and satisfactory customer support system is essential for the most successful online businesses to remain in business. Because AI chatbots are highly efficient, online businesses, virtual banking services, online casinos, and legal services rely on chatbots to handle the bulk of their customer service needs. Chatbots can run 24/7, already have a member’s history on file through the databases, and can provide far faster service than a human agent.
Chatbots are so efficient that many online businesses rely on them and maybe offer an optional email. This greatly allows these businesses to retool and shift funds from customer support to other vital areas to maintain profitability.
3. Fraud Detection
The nature of any online business is to receive payment for goods and services. Unfortunately, this simple procedure allows hackers or even bad members to commit fraud. Thanks again to AI, online businesses have a digital warrior best suited to detect fraud in real time. For example, thanks to behavioral AI, the online business knows each member’s normal and consistent payment patterns.
Therefore, if that member suddenly uses a new payment, the online business might request more information or ask the member to re-verify their account. Also, behavioral AI can spot in real time a member using another member’s payment details. In such cases, AI might immediately isolate that member from the network.
4. AI Delivers Personal Experiences
Tremendous effort and attention to detail go into producing a product that many online members can and will appreciate. However, statistics show members are more willing to engage if they feel a personal connection. Again, thanks to behavioral AI, it records a member’s habits—gaming and shopping preferences.
The result is personalized messages and ads directed to each member’s desires. For example, if you buy dress shirts, an online site that has an ad for socks probably won’t inspire you. However, a dynamic ad about discounted dress shirts will probably get you to open your wallet.
The Future about AI and Online Businesses
As technology improves, AI will only improve its models to better understand and respond to human behavior. As more online businesses turn to AI, look for more satisfied customers getting hooked on personalized experiences that traditional retail stores can’t provide.
Technology
From Admission to Graduation: Navigating Your Master of Science in Artificial Intelligence Journey

Key Takeaways:
- Understanding the admission requirements is crucial to get started on your AI journey.
- The curriculum covers various topics, from basic principles to advanced AI techniques.
- Balancing coursework, research, and practical experience is critical to a successful graduate experience.
- Networking and mentorship opportunities can significantly enhance your learning and career prospects.
- Upon graduation, many career paths in AI are available, ranging from academia to industry roles.
Table of Contents:
- Introduction
- Admission Requirements
- Curriculum Overview
- Balancing Coursework and Research
- Networking and Mentorship
- Career Opportunities After Graduation
- Conclusion
Introduction
The journey from admission to graduation in a Master of Science in Artificial Intelligence (AI) program is an exciting and transformative experience. This path not only equips you with technical know-how but also prepares you to tackle some of the most pressing challenges in the field. This article will guide you through each phase of obtaining your degree, providing insights and tips to help you succeed. Whether you’re just considering applying or already immersed in your studies, this comprehensive guide aims to support you in making the most of your educational journey.
Admission Requirements
Getting started on your masters in Artificial Intelligence journey begins with understanding the admission requirements. Generally, applicants need to have a strong foundation in mathematics and computer science. This often includes coursework in calculus, linear algebra, statistics, and programming languages like Python or Java. Additionally, most programs require GRE scores, letters of recommendation, a statement of purpose, and, in some cases, relevant work experience. It’s essential to thoroughly research the specific requirements of each program you’re interested in, as they can vary. Preparing a compelling application involves showcasing your academic qualifications, your passion for AI, and any relevant projects or work experience you may have.
Curriculum Overview
The curriculum for a Master of Science in AI is designed to provide a comprehensive understanding of both theoretical and practical aspects of artificial intelligence. Core courses typically include machine learning, natural language processing, computer vision, robotics, and data science. Elective courses allow you to specialize in deep learning, AI ethics, and AI for healthcare. Lab sessions and projects offer hands-on experience, enabling you to apply theoretical knowledge to real-world problems. Throughout the program, you will be exposed to the latest research and developments in AI, which will prepare you for both academic and industry roles. Graduate programs also often include a capstone project or thesis requirement, where you can dive deep into a particular area of interest and contribute original research or applications to the field.
Balancing Coursework and Research
One of the most challenging aspects of a graduate program is balancing coursework, research, and practical experience. Effective time management is crucial. Create a schedule accommodating class time, study sessions, and research activities. It’s also beneficial to start thinking about your thesis early on. Select a research topic that interests you and has ample resources and faculty support. Participating in internships or collaborative projects can provide valuable practical experience and enhance your resume. Additionally, taking advantage of available resources, such as academic support services and study groups, can help you stay on track. Remember that maintaining a balanced lifestyle is also essential; allocate time for relaxation and activities that help you de-stress, ensuring you remain focused and motivated throughout your program.
Networking and Mentorship
Networking and mentorship are invaluable components of your graduate experience. Attend conferences, workshops, and seminars to stay updated on the latest advancements in AI. These events also provide networking opportunities with professionals, researchers, and fellow students. Building a solid professional network can open up opportunities for collaborations, internships, and job placements. Moreover, seek mentors who can guide, support, and give feedback on your academic and career aspirations. Many programs offer formal mentoring schemes where you can be paired with faculty members or industry professionals. Engaging actively in discussions and being open to feedback can help you grow your expertise and career prospects exponentially. Additionally, consider joining AI-focused student organizations, online forums, and professional associations to broaden your network and access more resources.
Career Opportunities After Graduation
Upon graduation, a plethora of career paths in AI await you. Whether you’re interested in academia, research, or industry roles, the skills you’ve acquired will be highly sought after. In academia, you can pursue a Ph.D. or take up teaching roles. Industry positions range from AI researchers, data scientists, and machine learning engineers to AI ethics and policy-making roles. The technology sector, healthcare, finance, and creative industries increasingly seek AI expertise, making the job market diverse and expansive.
Furthermore, there are numerous emerging fields where AI is applied, such as autonomous vehicles, smart cities, and natural language generation. By staying abreast of market trends and continually enhancing your skills, you can find a career path that is both fulfilling and impactful. Many organizations also offer continuous education and professional development opportunities to ensure their AI professionals stay at the cutting edge of technology.
Conclusion
The journey through a Master of Science in Artificial Intelligence program is a rewarding endeavor that prepares you for a dynamic and impactful career. By understanding admission requirements, mastering the curriculum, balancing coursework with research, and leveraging networking opportunities, you can successfully navigate the challenges and reap the benefits of this transformative academic experience. As AI continues to evolve and integrate into various sectors, the knowledge and skills you acquire will place you at the forefront of innovation and progress. In this ever-changing field, your ability to adapt and continuously learn will be your greatest asset, equipping you to make meaningful contributions to society and the field of AI. Embrace the journey with determination and curiosity, and you will find yourself well-prepared to tackle the future of artificial intelligence.

 Business3 months ago
Business3 months agoTex9.Net Crypto: Fast, Secure International Money Transfers with Competitive Rates

 Entertainment2 months ago
Entertainment2 months agoSandra Orlow: Exploring the Life and Legacy of a Cultural Icon

 General1 week ago
General1 week agoBaby Alien Fan Bus: Watch Parts 2 & 3 on Twitter, Reddit!

 General1 week ago
General1 week agoDiana Nyad & Bart Springtime: A Swim to Success

 Business3 months ago
Business3 months agoSnapchat Planets: Exploring Your Streak Universe

 General1 month ago
General1 month agoDeeper Dive into myfavouriteplaces. org:// blog

 Business3 months ago
Business3 months agoFintechZoom Apple Stock: Real-Time Insights and Expert Analysis

 Entertainment3 months ago
Entertainment3 months agoUnlock Your Fantasy: Dive into Coomer Party Free OnlyFans Leaks!
















